Robots are the interface through which IT systems have a very concrete impact on the real world. Until now, dangers to humans and the environment have been minimised through strict isolation. With increasing networking, new technologies and forms of cooperation, this isolation is being broken down. This places new demands on cyber security. Until a few years ago, robots in industry were used almost exclusively behind protective barriers. The work areas of humans and robots were strictly isolated from each other. This rigid separation is being eliminated by new intelligent robot technology: so-called sensitive robots, which are able to perceive their environment and react to it with the help of control methods, are the key to cooperation between man and machine.
How humans and machines work together
There are three forms of collaboration: when a task can only be completed by humans and robots working together, i.e. each has to contribute its own special skills, this is called collaboration. An example would be placing a very heavy or hot object on a counterpart that is not always in the same place due to high manufacturing tolerances. The robot brings the necessary power and robustness, the human uses his visual skills to guide the robot to the correct position. True collaboration is still rare in industry, because full automation is often easier and cheaper in work steps that could be considered for it. The forms of collaboration that are currently being developed or are already integrated into manufacturing processes are usually cooperation or coexistence between humans and robots. In cooperation, they share a workplace, but never work simultaneously at the same place and on the same task. Rather, there are interfaces between sequential work processes; the steps complement each other. Coexistence, on the other hand, is when only the separating protective device is omitted, but the work processes of humans and robots do not overlap.
New technology, new risks
The automation of business processes leads to new risks. The topic of robotics safety is already on the digital agenda of many companies. All stakeholders – the board of directors, shareholders and customers – expect companies to pay sufficient attention to this challenge. This concerns physical security on the one hand, and information technology cyber security on the other. Companies must take into account that security and safety often pursue different goals: For example, while safety focuses on protecting the worker from the movements of a robot arm, security is necessary to protect the robot system from unauthorised human intervention. The area of security is facing new challenges in the context of process automation with the help of robots (RPA, see box). Companies are right to ask what cyber risks are associated with the use of automation technologies. After all, RPA provides hackers with new points of attack to expose, steal, alter or destroy sensitive data or information. In addition, unauthorised persons could access unauthorised applications and systems and exploit vulnerabilities to gain further access to the company’s data. Finally, there is the risk that a denial of service attack could bombard a company’s systems with so much information that production comes to a halt. (Compare Figure 1 using bots ) 
Figure 1
What companies can do
Given these risks, it is important that management takes the issue of cyber security seriously in the context of robotics deployment. Figure 2 shows cyber domains that are central to robotics security. This allows for sufficient prioritisation of the issue across the business and builds on existing security measures. Cyber security must be understood as a component of all operational and production processes and thus as a longitudinal issue. All employees – especially those who are part of the operational processes – should be aware of the existing threats and internalise appropriate behaviour.
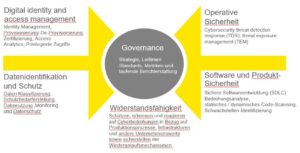 Figure 2
Figure 2
The selection of hardware and software already sets the course for a safe application of robotics in the company. The more digitalisation and networking progress, the more attention is paid to designing systems that are as free of vulnerabilities and as resistant to cyber attacks as possible, even during the development of hardware and software. In this case, one speaks of “security by design”. This is particularly important for complex systems and applications: Already during the conception of a robot application, potential vulnerabilities of the system must be identified through a structured analysis.
Strong design, but weak implementation
However, many vulnerabilities that are exploited in cyber attacks are not design flaws, but arise during implementation in the company. A first step to avoid security vulnerabilities is to analyse the computer codes used in the robot network. Numerous tools are available to companies for this purpose, which can be applied automatically within the framework of static code analysis. Since many applications are necessarily distributed in a network, the internal communication channels must be secured in the same way as data transmission to external systems. The fact that robots and sensors are physically connected to each other in a complex network, but also have a high degree of autonomy thanks to machine learning, makes this task particularly complex: a middleware layer ensures that sensors and robot arms, for example, can develop their functions independently of each other. This decoupling entails great security risks, since in this dynamic environment it is no longer possible to control who produces or consumes data. This also means that manipulation of the datafluss cannot be detected. One such middleware is the Robot Operating System (ROS); it is now increasingly found in industrial applications and robotics products. However, ROS does not currently provide any mechanisms for authentification, authorisation or ensuring data integrity – users need to be aware of this. Thus, robots based on ROS are inherently vulnerable to cyberattacks and tampering. However, approaches are currently being developed to better protect ROS applications from attackers. In future, it will be possible to issue certificates for individual elements in the network that prove their authenticity and also regulate their authorisation to send and receive data. In addition, companies must also ensure that the storage of data and access to the system are secured with appropriate measures. This includes aspects such as key and certificate storage as well as suitable workflows for maintenance. If certificates are not stored securely, securing communication is also pointless. It is equally important that changes are not simply made to the system, so during maintenance, which often does not take place on site but via external access, the personnel must also be authentified against the company’s network or the machine. Only then may maintenance be carried out via a secure channel. It is also advisable to keep an unalterable record of all actions during maintenance so that they can be traced later.
Resistance to cyber attacks is the goal
All these proactive measures serve to detect attacks and to be able to react to them quickly. However, organisational and technical means are also needed to minimise the consequences of a successful cyber attack and to ensure that production operations can be resumed quickly. The security of the entire system is thus the focus and must be defined as a common protection goal. This will also require new know-how for employees in networked production that goes far beyond classic IT security. Companies are facing major challenges. The realisation that they can become victims of cyber attacks at any time is an important first step. However, in order to operate successfully and responsibly in Industry 4.0, it is essential to select and implement the right security technologies together with competent partners.
How companies use robotic systems
Companies use the capability of robotic platforms to automate and coordinate workflows and perform cognitive learning functions. There is often confusion about what is meant by each when robotics is mentioned. Generally, the following three forms of robotics are used:
- Robotic Process Automation (RPA) is used to process manual tasks across different business processes and systems. Typical activities include data entry, data migration across multiple systems, data manipulation, data reconciliation and rule-based decision making in business processes.
- Orchestration (OR) focuses on the coordination of automation actions. An application example would be the coordination between different motion sensors and a robotic arm whose movements are constrained by the data from these sensors.
- Cognitive learning (CL) goes beyond rule-based decision-making and aims to perform complex tasks without human interaction. Self-learning algorithms are the basis for this. The goal of an application could be, for example, for robotic arms to learn from sensor data how large their movement radius is – up to the point where sensors would ultimately be superfluous.
 Create PDF
Create PDF

 Contributions as RSS
Contributions as RSS